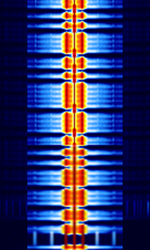
Adam H Secure Communication (AHSC)
From Signal Identification Wiki
AHSC works by encrypting the real data with a One-Time-Pad. This, theoretically, means that the data cannot be decoded if the message is not listened to in its entirety. (https://en.wikipedia.org/wiki/One-time_pad)
The transmission is split into two parts,
1. The data of the key 2. The data encrypted with the key
This means that if the receiver cannot receive the key or is late in recording / decoding the transmission, then the message cannot be decrypted and read.
Problems arise with this mode, however, since,
A. The real receiver must know the exact time in which the transmission will occur B. If the imposter receiver also knows the exact time, the security of the communication can, if the right software is used, be cracked
AHSC structure for transmission:[edit]
| Period | Purpose | Correlation |
|---|---|---|
| 800MS | Sync / Start | 400Hz |
| 200-300MS | Bit 0 [OTP] | 400Hz |
| 400-500MS | Bit 1 [OTP] | 400Hz |
| 700MS | End of OTP / Start of encrypted data | 400Hz |
| 200-300MS | Bit 0 [REAL DATA] | 400Hz |
| 400-500MS | Bit 1 [REAL DATA] | 400Hz |
| 800MS | Sync / End | 400Hz |
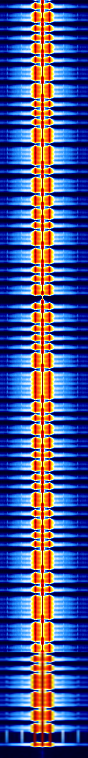
Large waterfall showing the entire transmission:[edit]
(Take note of the periodic space around the centre of the transmission that indicates the end of the OTP data and the start of the real, encrypted data)